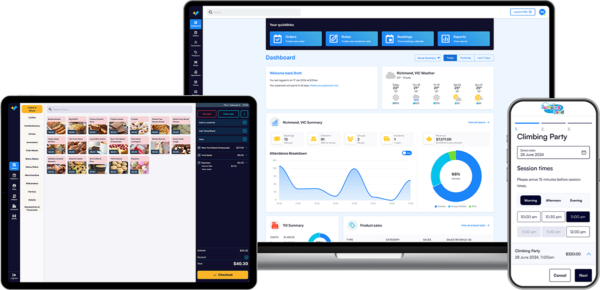
Control access to different functionalities based on user roles. Grant specific permissions to staff members and track their activities through user audits. Maintain accountability and prevent unauthorized access to critical data.
Role-based login access & user audits